MPC wallets use the principles of MPC cryptography, providing a tool that can be used to build large-scale, privacy-preserving applications. MPC allows an organization to perform computations without revealing each participant’s private input. Currently, MPC protocols can employ three Linear Secret Sharing Schemes (LSSS) types: additive secret sharing, Shamir secret sharing, and replicated secret sharing (CNF secret sharing). Additive secret sharing is mainly used in MPC protocols for dishonest majority settings, while Shamir and replicated secret sharing are used in honest majority MPC protocols. To achieve malicious security, additive secret sharing requires the configuration of information-theoretic Message Authentication Codes (MAC). CipherLab is dedicated to researching how to combine cryptography and blockchain technology to provide the most secure services. Let’s understand MAC.
What is MAC?
The concept of a Message Authentication Code (MAC) is a technique for confirming integrity and authentication, abbreviated as MAC. Using a MAC can verify whether the received message is the sender’s intention; that is, it can determine whether the message has been tampered with or if someone has impersonated the sender. The input of a MAC includes an arbitrary-length message and a secret key shared between the sender and receiver. The output is fixed-length data, which is the MAC value.
HMAC
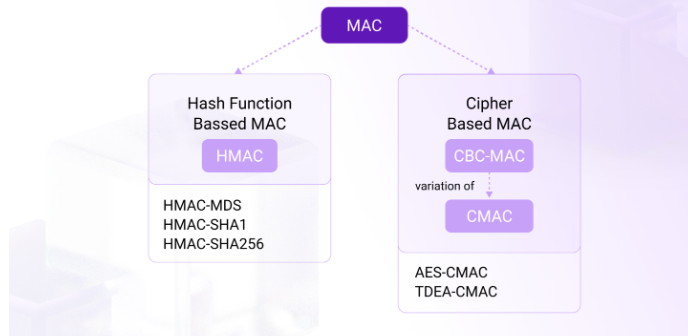
HMAC(Hash-BASED MAC) is a method for constructing a MAC using a one-way hash function. In HMAC, the “H” stands for Hash. Any strong one-way hash function can be used in HMAC, such as SHA-224, SHA-256, SHA-384, and SHA-512. The HMACs constructed from these hash functions are, respectively, HMAC-SHA-224, HMAC-SHA-256, HMAC-SHA-384, and HMAC-SHA-512.

CMAC
To address the security issues of non-fixed length messages, CMAC(Cipher-Based MAC) generates two sub-keys through critical expansion, which participate in the final message block encryption process. The CMAC computation process consists of three parts: sub-key generation, MAC generation, and MAC verification.
Comparison of HMAC and CMAC
In summary, HMAC and CMAC are both MACs used for message authentication but are implemented differently. HMAC is hash-based, while CMAC is block cipher-based. HMAC tends to be faster because it is based on hash functions. Both HMAC and CMAC can be used in embedded systems, although CMAC is more frequently used in such applications.
Two common types of MAC
Security Properties
MACs can prevent the forgery of authentication tags. As long as the key used in the MAC algorithm remains secret, it effectively prevents the creation of fake authentication tags. To avoid length extension attacks, serialization should be performed before using the MAC algorithm. The authentication tag should be at least 128 bits long to prevent collision and forgery issues. Although It requires a hash function output of 256 bits, a MAC algorithm, which uses a secret key, cannot be computed offline and must obtain the authentication tag directly from the server. Using a MAC alone for message authentication cannot detect replay attacks. It is advisable to include an incrementing counter in the MAC input or frequently change the shared key. Additionally, comparing two authentication tags must be done in constant time to prevent timing attacks.
Differences Between MAC and Digital Signature
A digital signature functions through an asymmetric key encryption system, offering integrity and non-repudiation. In this scheme, the sender creates a message signature with their private key and appends it to the message. The recipient can then authenticate the signature using the sender’s public key. Successful verification confirms that the stated sender indeed dispatched the message and that it remains unaltered. One primary distinction between MAC and digital signatures lies in the keys employed. While MAC relies on a symmetric key, necessitating the preservation of key secrecy between sender and receiver, digital signatures utilize an asymmetric key pair. This pair comprises a private key safeguarded by the signer and a publicly available key used by the recipient to validate the signature. Another contrast involves the security level provided. MAC algorithms generally operate faster and more efficiently compared to digital signature algorithms. Beyond confirming message integrity, digital signatures can also verify message origin, indicating the sender if their signature is present. Moreover, digital signatures enable asymmetric message verification: participants can validate whether a message has been altered without possessing the signing key.
CipherBC and MAC
In CipherBC, the application of MAC and secure connections is crucial. This allows for the creation of a large number of unique addresses for receiving and sending cryptocurrency, without the need for a separate private key for each address. MAC verifies message integrity and authenticity using a cryptographic hash function combined with a key to generate a unique authentication code. It ensurs data has not been tampered with during transmission. MAC also plays a vital role in deriving child private keys in HD wallets. In HD wallets, HMAC is used to introduce a deterministic random Chain Code during the derivation process of child nodes. This adds an extra layer of privacy protection to HD wallets. If the generation of child nodes relied solely on the parent node’s public key and the child node’s index, a hacker with access to the parent node’s public key could derive all child and grandchild public keys, compromising privacy.
About CipherBC
CipherBC stands as a market leader in digital asset custody and payment solutions. Catering to businesses seeking a secure and efficient transition to Web3 transformation, ensuring the security of assets and We are committed to the mission of “ fostering financial freedom.” In line with this objective, we provide asset owners with a complete range of services, encompassing asset custody, merchant payments, clearing and other financial services.

